Podcast (behind-the-woodshed): Play in new window | Download (Duration: 1:59:46 — 33.6MB) | Embed
BTWRLM208
Behind The Woodshed 3rd year Anniversary at Real Liberty Media
At the Situationally Aware Action Oriented Intelligence Center
Of Evolutionary Engagement

The Victory Against You in the Silent War is Your Silence
Big Mother, Not Big Brother
Engaging in counter-propaganda tactics and related work
What Glitters Is Only Goldish And Silvery
- The Royal Mint’s top-secret security patents behind the new £1 coin
- McCain introduces bill to update currency, eliminate penny
Sen. John McCain (R-AZ) and Senate Budget Committee Chairman Mike Enzi (R-WY) have reintroduced a bill that would modernize currency in the U.S.
According to a press release on McCain’s website, The Currency Optimization, Innovation, and National Savings Act of 2017 (COINS Act) would “modernize our currency by moving to a $1 dollar coin.”
Sen. Enzi says switching from a dollar bill to a dollar coin “could save our country $150 million a year.”
The COINS Act would also “reduce the cost of nickel production and suspend the minting of the penny, which currently costs more than one cent to produce.”
According to the press release, these changes “could generate up to $16 billion in taxpayer savings,” though details weren’t given on how long it would take to reach that number.
Future Crimetrails
- US scientists launch world’s biggest solar geoengineering study
Research programme will send aerosol injections into the earth’s upper atmosphere to study the risks and benefits of a future solar tech-fix for climate change
US scientists are set to send aerosol injections 20km up into the earth’s stratosphere in the world’s biggest solar geoengineering programme to date, to study the potential of a future tech-fix for global warming.
The $20m (£16m) Harvard University project will launch within weeks and aims to establish whether the technology can safely simulate the atmospheric cooling effects of a volcanic eruption, if a last ditch bid to halt climate change is one day needed.
Scientists hope to complete two small-scale dispersals of first water and then calcium carbonate particles by 2022. Future tests could involve seeding the sky with aluminium oxide – or even diamonds. This is not the first or the only university study,” said Gernot Wagner, the project’s co-founder, “but it is most certainly the largest, and the most comprehensive.”
Janos Pasztor, Ban Ki-moon’s assistant climate chief at the UN who now leads a geoengineering governance initiative, said that the Harvard scientists would only disperse minimal amounts of compounds in their tests, under strict university controls. - Geoengineering
- Fear of solar geoengineering is healthy – but don’t distort our research
Even if the world were to cut emissions to zero tomorrow, global temperatures and sea levels would rise for decades. If our roll of the climate dice is unlucky, they could rise for centuries. It is in this context that some climate researchers have begun to reluctantly take seriously ideas first proposed in the 1960s: the possibility of using solar geoengineering to help restore the world’s climate, alongside aggressive actions to reduce greenhouse-gas (GHG) emissions to zero and below.
Fear of solar geoengineering is entirely healthy. Its mere prospect might be hyped by fossil fuel interests to thwart emissions cuts. It could be used by one or a few nations in a way that’s harmful to many. There might be some yet undiscovered risk making the technology much less effective in reality than the largely positive story told by computer models.
Yet that healthy fear can distort discussion in unhealthy ways. A reader glancing at recent coverage in the Guardian, especially a piece by Martin Lukacs, might assume we were capitalistic tools of Donald Trump, eager to geoengineer the planet, democracy and justice be damned.
- A New [deceptive] Tool To Address Climate Change
- Sun’s impact on climate change quantified for first time
There is human-induced climate change, and there are natural climate fluctuations. One important factor in the unchanging rise and fall of the Earth’s temperature and its different cycles is the sun. As its activity varies, so does the intensity of the sunlight that reaches us. One of the key questions facing climate researchers is whether these fluctuations have any effect at all on the Earth’s climate. IPCC reports assume that recent solar activity is insignificant for climate change, and that the same will apply to activity in the near future.
Researchers from the Physical Meteorological Observatory Davos (PMOD), the Swiss Federal Institute of Aquatic Science and Technology (EAWAG), ETH Zurich and the University of Bern are now qualifying this assumption. Their elaborate model calculations are supplying a robust estimate of the contribution that the sun is expected to make to temperature change in the next 100 years. For the first time, a significant effect is apparent. They expect the Earth’s temperature to fall by half a degree when solar activity reaches its next minimum. - Donald Trump Supported Addressing Climate Change Before Calling It a ‘Hoax’
Presumptive GOP presidential nominee Donald Trump called for strong measures to address climate change as recently as 2009—a position in direct conflict with his numerous dismissals of the issue as a “hoax.”
Trump’s 2009 stance came in the form of an open letter to President Barack Obama and Congress published in the New York Times. The letter, first reported by Grist, was signed by Trump and other prominent business leaders in advance of the 2009 Copenhagen climate talks that most experts agree ended in failure. Trump’s children—Eric, Ivanka and Donald Jr.—all joined the letter as well.
“We support your effort to ensure meaningful and effective measures to control climate change, an immediate challenge facing the United States and the world today,” the letter says. “Please allow us, the United States of America, to serve in modeling the change necessary to protect humanity and our planet.”
Throughout the campaign Trump has challenged the urgency of addressing climate change using a variety of explanations from saying that the issue was “created by and for the Chinese” and that he believes climate change is merely weather. His energy policy proposals—to the extent that he has any—suggest a similar view. He has promised to “cancel” the Paris Agreement to address climate change and to expand the use of coal.
The letter is not the only inconsistency in Trump’s position on climate. The former reality TV star applied for a permit to build a seawall to protect the Trump International Golf Links & Hotel Ireland from rising sea levels due to “global warming and its effects.”
The Problem Is The Plan
- When the “Solutions” Become the Problems
Those benefiting from these destructive “solutions” may think the system can go on forever, but it cannot go on when every “solution” becomes a self-reinforcing problem that amplifies all the other systemic problems.
We are living in an interesting but by no means unique dynamic in which the solutions to problems such as slow growth and inequality have become the problems. This is a dynamic I have often discussed in various contexts. In essence, a solution that was optimized for an earlier era and situation is repeatedly applied to the present–but the present is unlike the past, and the old solution is no longer optimized to current conditions.The old solution isn’t just a less-than-optimal solution; it actively makes the problem worse.As a result, the old solution becomes a new problem that only exacerbates the current difficulties. The status quo strategy is not to question the efficacy of the old solution–it is to apply the old solution in heavier and heavier doses, on the theory that if only we increase the dose, it will finally resolve the problem. - DELINGPOLE: Scott Pruitt Is Failing to Drain the Swamp at the EPA
President Trump’s attempts to drain the swamp are being undermined by one of his key administrators.
Scott Pruitt, head of the Environmental Protection Agency, is more interested in building his political career than he is taking on the Green Blob, insiders report.
Pruitt is also said to be behind attempts to remove at least one of the key phrases from the president’s long-awaited Executive Order on the environment.
It concerns a proposal to repeal the EPA’s Endangerment Finding on CO2 (the disastrous, unscientific, job-killing ruling introduced during the Obama Administration, which rebranded the harmless trace gas Carbon Dioxide as a dangerous substance).
If Pruitt is successful and this clause is removed from the Executive Order it will represent a major setback for President Trump’s war with the Climate Industrial Complex. It may also put into jeopardy the promises Trump made on the campaign trail to scrap “any regulation that is outdated, unnecessary, bad for workers, or contrary to the national interest.”
“This is the president’s one shot at winning this battle,” an ally in the EPA camp warns. “It’s like the French heavy cavalry at Agincourt: lose momentum and he’s going to get stuck in the mud being shot to pieces by the English longbows.”
- Who Collaborates in Criminal Justice?
Collaborative justice seeks to overcome the limitations in traditional approaches to criminal justice issues by bringing together teams of stakeholders to share information, work toward the development of common goals, and jointly create policies to support those goals. Stakeholders are defined as those who have the power to influence the outcome of the problem at hand and have a demonstrated investment in doing so.
Ideally, teams should be comprised of the criminal justice agencies and community organizations that impact, or are impacted by, decisions that will be made by the collaborative team. Who should become part of the collaborative team will vary from jurisdiction to jurisdiction and will be influenced by the specific issues targeted by the team. Teams should think critically about their membership, and include individuals with the power to create change within their own agencies and organizations, or become “agents of change” within their communities. Representation by court community and criminal justice professionals is critical to the effectiveness of any criminal justice collaboration: judges, court administrators, prosecutors, defense attorneys, probation and parole representatives, corrections personnel, and law enforcement officers all play a part in the administration of justice, and bring valuable information, resources, and perspectives to a collaborative endeavor.
In addition to criminal justice system players, community and service providers should also be active participants in the collaboration in order for it to effectively address the complex social, behavioral, and health issues that are linked inextricably to the administration of criminal justice.
Real Mutha By Proxy
- Big Brother to spy on our internet history and ISP address without a warrant
Fight For The Future warns, by using the CRA to gut the FCC broadband privacy rules, lawmakers voted to allow ISPs to:
- Monitor and sell customer’s location data, search history, app usage, and browsing habits to advertisers without your permission
- Hijack customer’s search results, redirecting their traffic to paying third parties
- Insert ads into web pages that would otherwise not have them
Evan Greer, campaign director of Fight for the Future warns”Gutting these privacy rules won’t just allow Internet Service Providers to spy on us and sell our personal information, it will also enable more unconstitutional mass government surveillance…”The Electronic Frontier Foundation warns…
Should President Trump sign S.J. Res. 34 into law, big Internet providers will be given new powers to harvest your personal information in extraordinarily creepy ways. They will watch your every action online and create highly personalized and sensitive profiles for the highest bidder. All without your consent.
- Munchausen syndrome by proxy
Munchausen syndrome by proxy (MSbP or MbP) is a term often used when a caregiver or spouse fabricates, exaggerates, or induces mental or physical health problems in those who are in their care, with the primary motive of gaining attention or sympathy from others.[1] Its name is derived from the term Munchausen syndrome, a psychiatricfactitious disorder wherein those affected feign disease, illness, or psychological trauma to draw attention, sympathy, or reassurance to themselves. However, unlike in Munchausen syndrome, in MSbP, the deception involves not themselves, but rather someone under the person’s care. MSbP is primarily distinguished from other forms of abuse or neglect by the motives of the perpetrator. Some experts consider it to be an elusive, potentially lethal, and frequently misunderstood form of child abuse[2] or medical neglect.[3] However, others consider the concept to be problematic, since it is based largely on supposition regarding a person’s motives, which can be open to radically different interpretations.[4][5]
MSbP has also spawned much heated controversy within the legal and social services communities.
Black Market Recontrol
- Why American Farmers Are Hacking Their Tractors With Ukrainian Firmware
A dive into the thriving black market of John Deere tractor hacking.
To avoid the draconian locks that John Deere puts on the tractors they buy, farmers throughout America’s heartland have started hacking their equipment with firmware that’s cracked in Eastern Europe and traded on invite-only, paid online forums.
Tractor hacking is growing increasingly popular because John Deere and other manufacturers have made it impossible to perform “unauthorized” repair on farm equipment, which farmers see as an attack on their sovereignty and quite possibly an existential threat to their livelihood if their tractor breaks at an inopportune time.
“When crunch time comes and we break down, chances are we don’t have time to wait for a dealership employee to show up and fix it,” Danny Kluthe, a hog farmer in Nebraska, told his state legislature earlier this month. “Most all the new equipment [requires] a download [to fix].”
The nightmare scenario, and a fear I heard expressed over and over again in talking with farmers, is that John Deere could remotely shut down a tractor and there wouldn’t be anything a farmer could do about it.
“What you’ve got is technicians running around here with cracked Ukrainian John Deere software that they bought off the black market”
A license agreement John Deere required farmers to sign in October forbids nearly all repair and modification to farming equipment, and prevents farmers from suing for “crop loss, lost profits, loss of goodwill, loss of use of equipment … arising from the performance or non-performance of any aspect of the software.” The agreement applies to anyone who turns the key or otherwise uses a John Deere tractor with embedded software. It means that only John Deere dealerships and “authorized” repair shops can work on newer tractors.
Digital Over-exposure
- Digital driving licences on your phone by 2018 as ‘virtual reality’ tests explored to keep up with technology
Fumbling under the dashboard to find your driving license will soon be a thing of the past.
By next year motorists will be able to store digital licenses on their smartphones.
The Driver and Vehicle Licensing Agency (DVLA) will test the system this September and roll it out in spring 2018. - Certified Malice
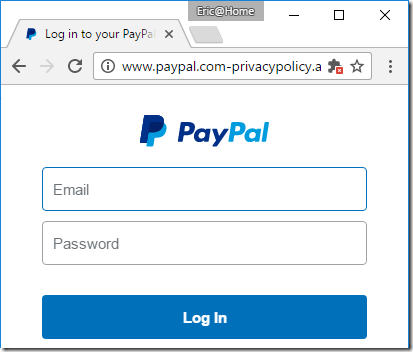
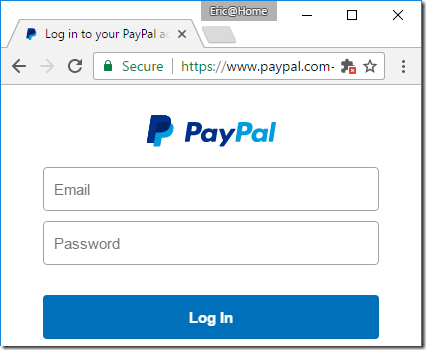
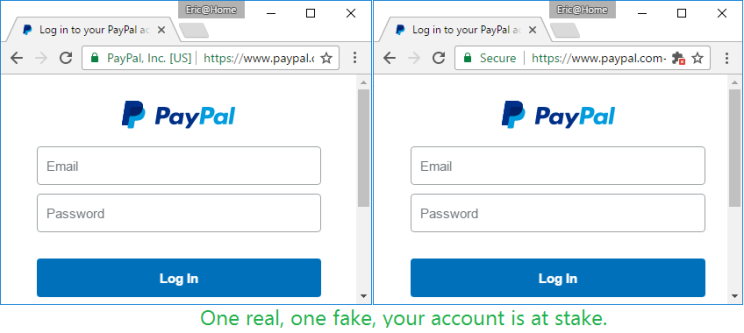
One unfortunate (albeit entirely predictable) consequence of making HTTPS certificates “fast, open, automated, and free” is that both good guys and bad guys alike will take advantage of the offer and obtain HTTPS certificates for their websites.
Today’s bad guys can easily turn a run-of-the-mill phishing spoof:

…into a somewhat more convincing version, by obtaining a free “domain validated” certificate and lighting up the green lock icon in the browser’s address bar:


The resulting phishing site looks almost identical to the real site:

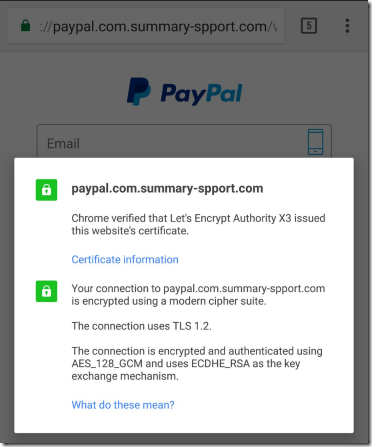
By December 8, 2016, LetsEncrypt had issued 409 certificates containing “Paypal” in the hostname; that number is up to 709 as of this morning. Other targets include BankOfAmerica (14 certificates), Apple, Amazon, American Express, Chase Bank, Microsoft, Google, and many other major brands. LetsEncrypt validates only that (at one point in time) the certificate applicant can publish on the target domain. The CA also grudgingly checks with the SafeBrowsing service to see if the target domain has already been blocked as malicious, although they “disagree” that this should be their responsibility. LetsEncrypt’s short position paper is worth a read; many reasonable people agree with it.
The “race to the bottom” in validation performed by CAs before issuing certificates is what led the IE team to spearhead the development of Extended Validation certificates over a decade ago. The hope was that, by putting the CAs name “on the line” (literally, the address line), CAs would be incentivized to do a thorough job vetting the identity of a site owner. Alas, my proposal that we prominently display the CAs name for all types (EV, OV, DV) of certificate wasn’t implemented, so domain validated certificates are largely anonymous commodities unless a user goes through the cumbersome process of manually inspecting a site’s certificates. For a number of reasons (to be explored in a future post), EV certificates never really took off.
Of course, certificate abuse isn’t limited to LetsEncrypt—other CAs have also issued domain-validated certificates to phishing sites as well:
- WikiLeaks Reveals “Marble”: Proof CIA Disguises Their Hacks As Russian, Chinese, Arabic…
WikiLeaks’ latest Vault 7 release contains a batch of documents, named ‘Marble’, which detail CIA hacking tactics and how they can misdirect forensic investigators from attributing viruses, trojans and hacking attacks to their agency by inserted code fragments in foreign languages. The tool was in use as recently as 2016. Per the WikiLeaks release:
“The source code shows that Marble has test examples not just in English but also in Chinese, Russian, Korean, Arabic and Farsi. This would permit a forensic attribution double game, for example by pretending that the spoken language of the malware creator was not American English, but Chinese, but then showing attempts to conceal the use of Chinese, drawing forensic investigators even more strongly to the wrong conclusion, — but there are other possibilities, such as hiding fake error messages.”RELEASE: CIA Vault 7 part 3 “Marble” https://t.co/M5NBFlXRu4 #Vault7 pic.twitter.com/HFyEf26FHK
— WikiLeaks (@wikileaks) March 31, 2017
The latest release is said to potentially allow for ‘thousands‘ of cyber attacks to be attributed to the CIA which were originally blamed on foreign governments.
WikiLeaks said Marble hides fragments of texts that would allow for the author of the malware to be identified. WikiLeaks stated the technique is the digital equivalent of a specialized CIA tool which disguises English language text on US produced weapons systems before they are provided to insurgents.It’s “designed to allow for flexible and easy-to-use obfuscation” as “string obfuscation algorithms” often link malware to a specific developer, according to the whistleblowing site.
The source code released reveals Marble contains test examples in Chinese, Russian, Korean, Arabic and Farsi.
“This would permit a forensic attribution double game, for example by pretending that the spoken language of the malware creator was not American English, but Chinese, but then showing attempts to conceal the use of Chinese, drawing forensic investigators even more strongly to the wrong conclusion,” WikiLeaks explains, “But there are other possibilities, such as hiding fake error messages.”
The code also contains a ‘deobfuscator’ which allows the CIA text obfuscation to be reversed. “Combined with the revealed obfuscation techniques, a pattern or signature emerges which can assist forensic investigators attribute previous hacking attacks and viruses to the CIA.”
Previous Vault7 releases have referred to the CIA’s ability to mask its hacking fingerprints.
WikiLeaks claims the latest release will allow for thousands of viruses and hacking attacks to be attributed to the CIA.
CIA’s “Marble Framework” shows its hackers use potential decoy languages https://t.co/Hm3pTPSXIS
Background: https://t.co/GsoN4BuyTz pic.twitter.com/ZT66doCnfY
— WikiLeaks (@wikileaks) March 31, 2017
And the rabbit hole just got even deeper.
- CrowdStrike Revises and Retracts Parts of Explosive Russian Hacking Report
Last week, I published two posts on cyber security firm CrowdStrike after becoming aware of inaccuracies in one of its key reports used to bolster the claim that operatives of the Russian government had hacked into the DNC. This is extremely important since the DNC hired CrowdStrike to look into its hack, and at the same time denied FBI access to its servers.
Before reading any further, you should read last week’s articles if you missed them the first time.
Credibility of Cyber Firm that Claimed Russia Hacked the DNC Comes Under Serious Question
Now here are the latest developments courtesy of Voice of America:
U.S. cybersecurity firm CrowdStrike has revised and retracted statements it used to buttress claims of Russian hacking during last year’s American presidential election campaign. The shift followed a VOA report that the company misrepresented data published by an influential British think tank.
In December, CrowdStrike said it found evidence that Russians hacked into a Ukrainian artillery app, contributing to heavy losses of howitzers in Ukraine’s war with pro-Russian separatists.
VOA reported Tuesday that the International Institute for Strategic Studies (IISS), which publishes an annual reference estimating the strength of world armed forces, disavowed the CrowdStrike report and said it had never been contacted by the company.
CrowdStrike was first to link hacks of Democratic Party computers to Russian actors last year, but some cybersecurity experts have questioned its evidence. The company has come under fire from some Republicans who say charges of Kremlin meddling in the election are overblown.
After CrowdStrike released its Ukraine report, company co-founder Dmitri Alperovitch claimed it provided added evidence of Russian election interference. In both hacks, he said, the company found malware used by “Fancy Bear,” a group with ties to Russian intelligence agencies.
CrowdStrike’s claims of heavy Ukrainian artillery losses were widely circulated in U.S. media.
On Thursday, CrowdStrike walked back key parts of its Ukraine report.
The company removed language that said Ukraine’s artillery lost 80 percent of the Soviet-era D-30 howitzers, which used aiming software that purportedly was hacked. Instead, the revised report cites figures of 15 to 20 percent losses in combat operations, attributing the figures to IISS.
Finally, CrowdStrike deleted a statement saying “deployment of this malware-infected application may have contributed to the high-loss nature of this platform” — meaning the howitzers — and excised a link sourcing its IISS data to a blogger in Russia-occupied Crimea.
In an email, CrowdStrike spokeswoman Ilina Dmitrova said the new estimates of Ukrainian artillery losses resulted from conversations with Henry Boyd, an IISS research associate for defense and military analysis. She declined to say what prompted the contact.
Dmitrova noted that the FBI and the U.S. intelligence community have also concluded that Russia was behind the hacks of the Democratic National Committee, Democratic Congressional Campaign Committee and the email account of John Podesta, Hillary Clinton’s campaign manager.
Here’s the problem. Yes, the FBI has agreed with CrowdStrike’s conclusion, but the FBI did not analyze the DNC servers because the DNC specifically denied the FBI access. This was noteworthy in its own right, but it takes on vastly increased significance given the serious errors in a related hacking report produced by the company.
As such, serious questions need to be asked. Why did FBI head James Comey outsource his job to CrowdStrike, and why did he heap praise on the company? For instance, back in January, Comey referred to CrowdStrike as a “highly respected private company.”
- James Comey’s New Idea: An International Encryption Backdoor Partnership
FBI Director James Comey is still pitching encryption backdoors, despite there being almost no one — from the Intelligence Community to legislators around the world — interested in what he’s selling. Comey claims to be sitting on a pile of encrypted devices the FBI can’t get into, even with help from outside contractors.
His latest backdoor idea was floated at a national security symposium at the University of Texas. Knowing any legislated backdoors might result in US device customers turning to overseas suppliers, Comey thinks he can minimize domestic fiscal damage by getting the rest of the world to fall in line with an idea most foreign governments still find unpalatable, even as they suffer terrorist attacks with a far greater frequency than we do at home. Michael Kan has more details at ComputerWorld:
Speaking on Thursday, Comey suggested that the U.S. might work with other countries on a “framework” for creating legal access to encrypted tech devices.
“I could imagine a community of nations committed to the rule of law developing a set of norms, a framework, for when government access is appropriate,” he said on Thursday.
Comey doesn’t say how he plans to set this in motion. He’s had no luck on the domestic front, so hoping for an “international framework” to spring into existence is, at best, inordinately hopeful. He directly addressed one of the many concerns device makers have about encryption backdoors, stating he had no desire to “chase innovation” out of the US. But that doesn’t mean he’s not interested in harming US innovation. He simply believes every country in the partnership should suffer equally.
As always happens when Comey opens his mouth about encryption, plenty of experts in the field are on hand to criticize his comments.
“I don’t think it makes sense,” said Nicholas Weaver, a researcher at the International Computer Science Institute at the University of California Berkeley.
Comey’s idea means that all countries will essentially agree to weaken the security in their vendors’ tech products, Weaver said. However, other countries will balk, fearing that the U.S. might exploit the cooperation for spying purposes.
“Would you still use a U.S. product, even if you know the NSA (National Security Agency) could have the rights to it?” he said.
Most of our allies around the world are still stinging a bit from multiple national security leaks — some of which have exposed nearly as much intrusiveness of their own security agencies as they have about the NSA’s reach and grasp. With the NSA heavily-involved in diverting hardware shipments to implant backdoors, no one’s in any hurry to add their country to the list of “buyer beware” electronics.
- UPDATE: Verizon Software on Android Phones
UPDATE: We have received additional information from Verizon and based on that information we are withdrawing this post while we investigate further. Here is the statement from Kelly Crummey, Director of Corporate Communications of Verizon: “As we said earlier this week, we are testing AppFlash to make app discovery better for consumers. The test is on a single phone – LG K20 V – and you have to opt-in to use the app. Or, you can easily disable the app. Nobody is required to use it. Verizon is committed to your privacy. Visit www.verizon.com/about/privacy to view our Privacy Policy.”
Within days of Congress repealing online privacy protections, Verizon has announced new plans to install software on customers’ devices to track what apps customers have downloaded. With this spyware, Verizon will be able to sell ads to you across the Internet based on things like which bank you use and whether you’ve downloaded a fertility app.Verizon’s use of “AppFlash”—an app launcher and web search utility that Verizon will be rolling out to their subscribers’ Android devices “in the coming weeks”—is just the latest display of wireless carriers’ stunning willingness to compromise the security and privacy of their customers by installing spyware on end devices.The AppFlash Privacy Policy published by Verizon states that the app can be used to“collect information about your device and your use of the AppFlash services. This information includes your mobile number, device identifiers, device type and operating system, and information about the AppFlash features and services you use and your interactions with them. We also access information about the list of apps you have on your device.”Troubling as it may be to collect intimate details about what apps you have installed, the policy also illustrates Verizon’s intent to gather location and contact information:“AppFlash also collects information about your device’s precise location from your device operating system as well as contact information you store on your device.”And what will Verizon use all of this information for? Why, targeted advertising on third-party websites, of course:“AppFlash information may be shared within the Verizon family of companies, including companies like AOL who may use it to help provide more relevant advertising within the AppFlash experiences and in other places, including non-Verizon sites, services and devices.”In other words, our prediction that mobile Internet providers would start installing spyware on their customers’ phones has come true, less than 48 hours after Congress sold out your personal data to companies like Comcast and AT&T. With the announcement of AppFlash, Verizon has made clear that it intends to start monetizing its customers’ private data as soon as possible.
Stop Privacy Invasion
- Minnesota Senate votes 58-9 to pass Internet privacy protections in response to repeal of FCC privacy rules
f
In stark contrast to Congress’s recent vote against the Internet privacy rights of American constituents, Minnesota’s state Senators have voted to add broadband privacy protections at the state level. The protections were added in an amendment to S.F. No. 1937, the Minnesota economic development budget bill, by Minnesota State Sen. Latz. This Internet privacy amendment was introduced as a direct response to the Tuesday 215-205 vote by the House of Representatives for S.J.Res. 34. FCC Internet privacy rules would have come into effect at the end of 2016 and would have forced Internet service providers (ISPs) and telecoms to get permission before selling your private internet history or app data usage, which they also don’t consider sensitive information. These telecoms and ISPs have long been hard at work to dismantle Internet privacy with their words and money – but they have now been stopped in one more state.
In direct response to Congress, Minnesota passes Internet privacy protections
Once this bill passes in the Minnesota House and is signed into law by Governor Mark Dayton, ISPs will be required to obtain “express written approval from the customer” before collecting customer information from their users. Furthermore, it forbids these ISPs and telecoms from refusing to provide service to someone that refuses to approve the collection of their personal data; which, if the online reaction to the repeal of FCC privacy rules is any show of, is a lot of people. The full text of the amendment to S.F. No. 1937 is:
Gangrenous Wounds
- How the FBI Played a Central Role in the First ISIS Attack on U.S. Soil
Investigation finds an undercover agent encouraged a shooter in Garland to “tear up Texas.” It gets worse.
The first attack on U.S. soil for which ISIS claimed responsibility—a 2015 shooting in Garland, Texas—was instigated by the FBI, according to an investigation by CBS’ “60 Minutes” and government documents obtained by an attorney involved in the case.
In a macabre twist, an undercover FBI agent who encouraged one of the shooters to “tear up Texas” was also physically present at the scene of the crime, mere feet away from the shooters.
Prior to that, a separate informant was paid $132,000 by the FBI to pretend for three years to be friends with the future shooter. When the man found out his supposed friend had taped more than 1,500 hours of their conversations on behalf of the intelligence agency, he withdrew from his religious community and eventually fell into online religious extremism.
An FBI trainer suggested in an interview with “60 Minutes” that, had the attack been bigger, the agency’s numerous ties to the shooter would have led to a congressional investigation.
As lurid as this sounds, it fits with the findings of human rights organizations, which have noted the FBI has a long history of pushing Muslim Americans into alleged terror plots they might not have otherwise been engaged in or connected to.
On May 3, 2015, two Islamist extremist gunmen opened fire at an exhibit for cartoons of the Islamic prophet Muhammad in Garland, Texas. The contest featured key figures in the Islamophobia industry, including anti-Muslim demagogue Pamela Geller and extreme-right Dutch politician Geert Wilders.
The intentionally provocative exhibit was swarming with security, including dozens of police officers, snipers and a SWAT team. The heavily armed attackers injured a security guard outside the building before they were themselves promptly shot by snipers and killed.
ISIS soon after took credit for the shooting. There is no evidence that ISIS organized the attack, but the shooters had been independently radicalized and were inspired by the genocidal extremist group.
In the two years since, the Garland shooting has been used to justify a vast array of anti-Muslim policies and measures.
A new investigation by the investigation team at “60 Minutes,” nevertheless, shows that the FBI was deeply implicated in the attack.
- McCain Furious At Rex Tillerson For Saying Assad Can Stay
The six year Syrian proxy war to dethrone president Bashar al Assad quietly ended with a whimper yesterday when at a news conference in the Turkish capital, Secretary of State Rex Tillerson suggested the end of Bashar Assad’s presidency is no longer a prerequisite for a way out of the Syrian crisis, in a dramatic U-turn from Washington’s long-held policy.
“I think the longer term status of President Assad will be decided by the Syrian people,” said Tillerson at a joint conference with Turkish Foreign Minister Mevut Cavusoglu on Thursday, AFP reported. Later, UN Ambassador Nikki Haley echoed Tillerson, saying “Our priority is no longer to sit and focus on getting Assad out.”
“You pick and choose your battles and when we’re looking at this, it’s about changing up priorities and our priority is no longer to sit there and focus on getting Assad out,” U.S. Ambassador Nikki Haley told a small group of reporters.“Do we think he’s a hindrance? Yes. Are we going to sit there and focus on getting him out? No,” she said. “What we are going to focus on is putting the pressure in there so that we can start to make a change in Syria.”
Under President Barack Obama, the United States made Assad’s departure one of its key objectives. The Syrian armed opposition also insisted upon the longtime leader’s resignation as one of the conditions during the Astana peace talks.
For those unaware, allowing the people of Syria to decide the fate of President Assad has been Russia’s stance since the conflict began. Moscow has repeatedly rebuffed any preconditions for Assad to step down before a political settlement of the crisis.
“The UN Security Council resolution and various decisions on Syria, adopted since 2012 with our proactive involvement, contain no demand or hint that Syrian President Bashar al-Assad must resign. On the contrary, they say that the people of Syria alone have a right to decide their future, and that the political process should involve all forces of Syrian society without exception, including ethnic, political forces, religious denominations and all opposition groups,” Russian Foreign Minister Sergey Lavrov said in a 2016 interview.
In other words, the entire proxy conflict, with thousands of lives lost, and millions of Syrian immigrants flooding Europe, has been for nothing.
Hot Diggity Doge

The DOGE OF WAR
D8rgRZjcBPLAhvmUazYXxCZasueoEmP7VGUnleash the Power of the DOGE OF WAR
Please Donate to RLM
In This Doge Eat Doge World
Secure Private Alternative To Skype
Tox: Client Side only as of 4/15/2016
Jitsi:
Dump Skype – Piss Off The NSA
Silent Weapons for Quiet Wars
- The people know that they have created this farce and financed it with their own taxes (consent), but they would rather knuckle under than be the hypocrite. Factor VI – Cattle Those who will not use their brains are no better off than those who have no brains, and so this mindless school of jelly-fish, father, mother, son, and daughter, become useful beasts of burden or trainers of the same.
- Mr. Rothschild’s Energy Discovery
What Mr. Rothschild [2] had discovered was the basic principle of power, influence, and control over people as applied to economics. That principle is “when you assume the appearance of power, people soon give it to you.”
Listen How
The Law of War
General Orders No. 100: The Lieber Code
INSTRUCTIONS FOR THE GOVERNMENT OF ARMIES OF THE UNITED STATES IN THE FIELD
Where Not Throwing Oppression Off, You Live Either Under an Occupation or by Conquest.
The Choice and Responsibility are Yours. United We Strike
Behind The Woodshed for that practical education & hard but necessary dose of reality.
Spread The Word Behind The Woodshed.
(^_^)






![[Most Recent Charts from www.kitco.com]](https://www.kitconet.com/charts/metals/gold/t24_au_en_usoz_4.gif)